Kubernetes > Service Accounts
Service Accounts reside inside Namespaces
There will be a ‘default’ Service Account inside the ‘default’ NameSpace
If a Pod has to contact the API server, it would do so through the Service Account it’s associated with, through the credentials that the ServiceAccount provides
To view the list of Service Accounts, implicitly in the ‘default' namespace
[root@master cka]# kubectl get sa
NAME SECRETS AGE
default 1 47h
Note: If the namespace is not specified it would assume the default namespace
To view the list of service accounts, explicitly in the ‘default’ namespace
[root@master cka]# kubectl get sa --namespace default
NAME SECRETS AGE
default 1 47h
Let’s launch a Pod imperatively
[root@master cka]# kubectl run test-pod --generator=run-pod/v1 --image=httpd
pod/test-pod created
[root@master cka]# kubectl get pods
NAME READY STATUS RESTARTS AGE
test-pod 1/1 Running 0 13s
To view more details of the Pod and subsequently filter the serviceAccount and namespace names
[root@master cka]# kubectl get po/test-pod -o yaml | grep serviceAccountName
serviceAccountName: default
[root@master cka]# kubectl get po/test-pod -o yaml | grep namespace:
namespace: default
Let’s define a ServiceAccount configuration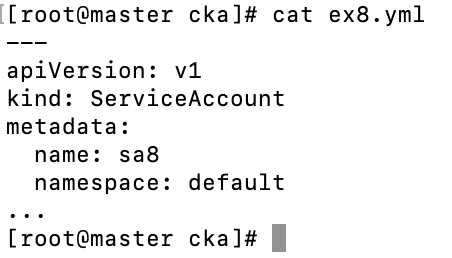
Let’s create it
[root@master cka]# kubectl create -f ex8.yml
serviceaccount/sa8 created
To view the list of ServiceAccounts again]
[root@master cka]# kubectl get sa
NAME SECRETS AGE
default 1 47h
sa8 1 31s
To view more details about the ServiceAccount
[root@master cka]# kubectl get sa sa8 -o yaml
apiVersion: v1
kind: ServiceAccount
metadata:
creationTimestamp: "2019-04-03T12:26:49Z"
name: sa8
namespace: default
resourceVersion: "248768"
selfLink: /api/v1/namespaces/default/serviceaccounts/sa8
uid: c14f12f7-560b-11e9-a3f2-5668a099244e
secrets:
- name: sa8-token-7bdqc
A secret is automatically generated, and this secret will be used by objects under the service account, such as Pods to access the API server
Let’s define a Pod configuration, and associate it with serviceAccount ’sa8'
[root@master cka]# cat ex8~.yml
---
apiVersion: v1
kind: Pod
metadata:
name: pod8
namespace: default
spec:
serviceAccountName: sa8
containers:
- name: ctr8
image: httpd
...
Let’s create the Pod
[root@master cka]# kubectl create -f ex8~.yml
pod/pod8 created
The Pod is now running
[root@master cka]# kubectl get pod/pod8
NAME READY STATUS RESTARTS AGE
pod8 1/1 Running 0 31s
To verify the serviceAccount details of the Pod
[root@master cka]# kubectl get pods/pod8 -o yaml | grep serviceAccount
serviceAccount: sa8
serviceAccountName: sa8
We see the secret associated with sa8 is being used by pod8
[root@master cka]# kubectl get pods/pod8 -o yaml | grep secretName
secretName: sa8-token-7bdqc
Clean up
[root@master cka]# kubectl delete sa sa8 ; kubectl delete pods --all
serviceaccount "sa8" deleted
pod "test-pod" deleted
## end of post ##